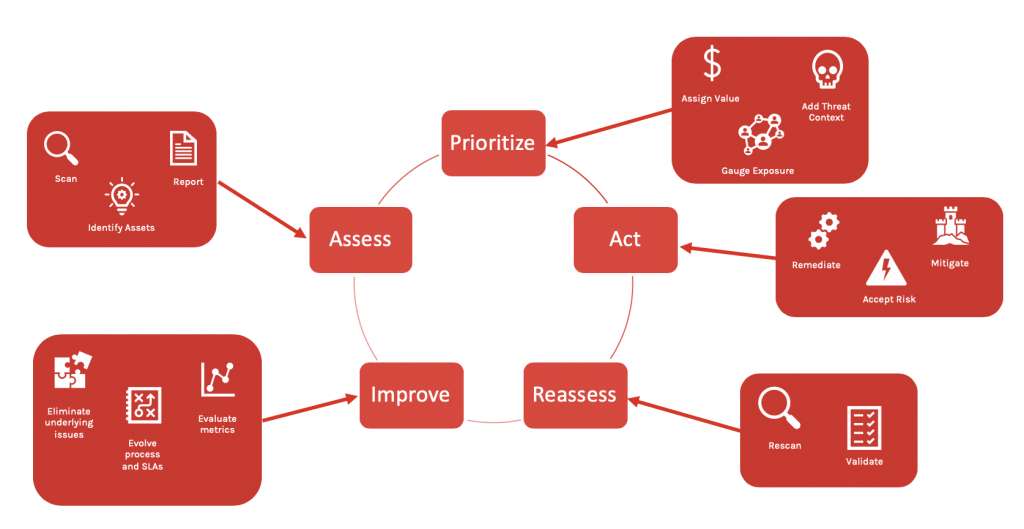
Introduction
In today’s rapidly evolving threat landscape, security teams face an overwhelming volume of data from diverse sources. Logs, alerts, vulnerability reports, and threat intelligence feeds generate terabytes of information that need to be collected, processed, and analyzed effectively. Elasticsearch has emerged as a powerful tool in the cybersecurity arsenal, enabling teams to harness this data deluge and transform it into actionable intelligence.
This article explores the various applications of Elasticsearch in cybersecurity operations, from vulnerability management to threat hunting and incident response. We’ll dive into practical implementations and examine real-world examples of how organizations are leveraging this technology to strengthen their security posture.
Vulnerability Management with Elasticsearch
Data Centralization
Elasticsearch provides a centralized repository for storing vulnerability data from disparate sources like threat intelligence feeds, asset inventory lists, application and system audits, and penetration testing reports. By consolidating this data, security operations teams can obtain an overarching view of their organization’s vulnerabilities and prioritize remediation efforts accordingly.
Example Implementation:
PUT /vulnerabilities/_doc/CVE-2023-12345
{
"cve_id": "CVE-2023-12345",
"description": "Buffer overflow vulnerability in Example Software v2.1",
"source": "NVD",
"cvss_score": 8.9,
"affected_systems": ["web-server-01", "web-server-02"],
"remediation_status": "pending",
"discovery_date": "2023-05-01",
"patch_available": true,
"patch_link": "https://example.com/patches/12345",
"asset_criticality": "high"
}
Automatic Parsing
As soon as new vulnerabilities are discovered or updated, they must go through manual triage, which requires extensive human effort and often leads to delays. Elasticsearch can automatically parse vulnerability data streams from various sources (e.g., CVE, NVD, OSVDB, MITRE ATT&CK) to extract necessary contextual attributes. Then, it assigns scores or severity ratings based on predefined rules tailored to each organization’s unique environment.
Example: Using Logstash to Parse NVD Data Feeds
input {
http_poller {
urls => {
nvd_feed => "https://nvd.nist.gov/feeds/json/cve/1.1/nvdcve-1.1-recent.json.gz"
}
request_timeout => 60
schedule => { cron => "0 */12 * * *" } # Poll every 12 hours
codec => "json"
}
}
filter {
json {
source => "message"
target => "nvd_data"
}
ruby {
code => '
event.set("cves", [])
nvd_data = event.get("nvd_data")
if nvd_data && nvd_data["CVE_Items"]
nvd_data["CVE_Items"].each do |cve_item|
cve = {}
cve["id"] = cve_item["cve"]["CVE_data_meta"]["ID"]
cve["description"] = cve_item["cve"]["description"]["description_data"].first["value"]
# Extract CVSS v3 score if available
if cve_item["impact"] && cve_item["impact"]["baseMetricV3"]
cve["cvss_score"] = cve_item["impact"]["baseMetricV3"]["cvssV3"]["baseScore"]
cve["severity"] = cve_item["impact"]["baseMetricV3"]["cvssV3"]["baseSeverity"]
end
# Add to the array
event.get("cves") << cve
end
end
'
}
}
output {
elasticsearch {
hosts => ["localhost:9200"]
index => "vulnerability_feed"
document_id => "%{[cve][id]}"
}
}
Enhanced Visibility
Elasticsearch indexes vulnerability records, allowing users to perform full-text queries, faceted navigation, and sorting. This capability provides enhanced visibility into the types, origins, and impact levels of the identified vulnerabilities, empowering administrators to focus attention on problem areas more precisely.
Example Query: Find High-Risk Vulnerabilities Affecting Critical Systems
GET /vulnerabilities/_search
{
"query": {
"bool": {
"must": [
{ "range": { "cvss_score": { "gte": 7.0 } } },
{ "term": { "asset_criticality": "high" } },
{ "term": { "remediation_status": "pending" } }
]
}
},
"sort": [
{ "cvss_score": { "order": "desc" } }
],
"aggs": {
"affected_systems_count": {
"terms": {
"field": "affected_systems.keyword",
"size": 10
}
},
"vulnerability_types": {
"terms": {
"field": "vulnerability_type.keyword",
"size": 5
}
}
}
}
This query returns high-risk vulnerabilities (CVSS score ≥ 7.0) affecting critical systems that are still pending remediation, sorted by severity. It also provides aggregations to understand which systems are most affected and what types of vulnerabilities are most prevalent.
Adaptive Workflow Orchestration
Integration with Elasticsearch enables orchestration tools like open-source OSBase, Demisto, and Phantom Cyber to dynamically adjust their workstreams based on the current state of known vulnerabilities. This adaptive approach ensures that security practitioners always tackle high-priority weaknesses first while minimizing resource wastage on already-resolved issues.
Example: Webhook Trigger for Vulnerability Orchestration
PUT _watcher/watch/high_severity_vuln
{
"trigger": {
"schedule": {
"interval": "1h"
}
},
"input": {
"search": {
"request": {
"indices": ["vulnerabilities"],
"body": {
"query": {
"bool": {
"must": [
{ "range": { "cvss_score": { "gte": 9.0 } } },
{ "term": { "remediation_status": "pending" } },
{ "term": { "patch_available": true } }
]
}
}
}
}
}
},
"condition": {
"compare": {
"ctx.payload.hits.total": {
"gt": 0
}
}
},
"actions": {
"webhook": {
"webhook": {
"scheme": "https",
"host": "orchestration.example.com",
"port": 443,
"method": "post",
"path": "/api/triggers/vulnerability",
"params": {},
"headers": {
"Content-Type": "application/json"
},
"body": "ctx.payload.hits.hits"
}
}
}
}
Personalized Notifications
Leveraging machine learning capabilities, Elasticsearch can assist in generating personalized notification strategies based on system ownership, vulnerability context, and historical response patterns. This ensures that the right information reaches the right teams at the right time.
Example: Customized Alerts Based on Team Responsibility
PUT _watcher/watch/team_specific_alerts
{
"trigger": { "schedule": { "interval": "1d" } },
"input": {
"search": {
"request": {
"indices": ["vulnerabilities"],
"body": {
"query": {
"bool": {
"must": [
{ "term": { "remediation_status": "pending" } },
{ "range": { "discovery_date": { "gte": "now-7d" } } }
]
}
}
}
}
}
},
"condition": { "compare": { "ctx.payload.hits.total": { "gt": 0 } } },
"transform": {
"script": {
"source": """
def teamAlerts = [:];
for (hit in ctx.payload.hits.hits) {
def vuln = hit._source;
def system = vuln.affected_systems;
if (system.contains("web-server")) {
if (!teamAlerts.containsKey("web_team")) {
teamAlerts.web_team = [];
}
teamAlerts.web_team.add(vuln);
} else if (system.contains("db-server")) {
if (!teamAlerts.containsKey("db_team")) {
teamAlerts.db_team = [];
}
teamAlerts.db_team.add(vuln);
}
// Add more team mappings as needed
}
return [ "team_alerts": teamAlerts ];
"""
}
},
"actions": {
"notify_web_team": {
"condition": { "script": "return ctx.payload.team_alerts.containsKey('web_team')" },
"email": {
"to": "web-team@example.com",
"subject": "New Vulnerabilities Affecting Web Systems",
"body": {
"html": """
<h2>Web System Vulnerabilities Requiring Attention</h2>
<table>
<tr><th>CVE</th><th>Severity</th><th>Systems</th></tr>
<tr>
<td></td>
<td></td>
<td></td>
</tr>
</table>
"""
}
}
},
"notify_db_team": {
"condition": { "script": "return ctx.payload.team_alerts.containsKey('db_team')" },
"email": {
"to": "db-team@example.com",
"subject": "New Vulnerabilities Affecting Database Systems",
"body": {
"html": """
<h2>Database System Vulnerabilities Requiring Attention</h2>
<table>
<tr><th>CVE</th><th>Severity</th><th>Systems</th></tr>
<tr>
<td></td>
<td></td>
<td></td>
</tr>
</table>
"""
}
}
}
}
}
Security Information and Event Management (SIEM) Use Cases
Beyond vulnerability management, Elasticsearch forms the backbone of many SIEM solutions, including the popular Elastic Security (formerly Elastic SIEM). Here are some key use cases:
Log Aggregation and Analysis
Elasticsearch excels at collecting and processing massive volumes of logs from various sources, enabling security teams to perform real-time analysis and historical investigations.
Example: Filebeat Configuration for Collecting Windows Security Logs
filebeat.inputs:
- type: winlog
name: windows-security
event_logs:
- name: Security
ignore_older: 72h
level: information
processors:
- script:
lang: javascript
id: security_enrichment
file: ${path.home}/scripts/enrich_windows_events.js
output.elasticsearch:
hosts: ["elasticsearch:9200"]
index: "winlogbeat-%{[agent.version]}-%{+yyyy.MM.dd}"
pipeline: "windows-security-enrichment"
Threat Detection and Alerting
Elasticsearch’s search capabilities and rule engines can identify suspicious patterns and trigger alerts based on predefined detection rules.
Example: Detection Rule for Brute Force Attempts
{
"rule_id": "brute-force-detection",
"risk_score": 75,
"description": "Detects multiple failed login attempts from the same source IP",
"name": "Potential Brute Force Attack",
"severity": "high",
"type": "threshold",
"query": "event.category:authentication AND event.outcome:failure",
"threshold": {
"field": "source.ip",
"value": 5,
"cardinality": [
{
"field": "user.name",
"value": 3
}
]
},
"timeline_id": "auth-timeline",
"timeline_title": "Authentication Timeline",
"false_positives": ["Password resets", "New systems onboarding"],
"tags": ["brute-force", "authentication"]
}
Anomaly Detection
Elasticsearch’s machine learning capabilities can identify unusual patterns that might indicate compromised accounts, data exfiltration, or other security incidents.
Example: Machine Learning Job for Anomalous Login Patterns
PUT _ml/anomaly_detectors/unusual_login_times
{
"description": "Detect unusual login times for users",
"analysis_config": {
"bucket_span": "1h",
"detectors": [
{
"detector_description": "Unusual login time",
"function": "rare",
"by_field_name": "user.name",
"over_field_name": "event.start_time.hour_of_day"
}
],
"influencers": ["user.name", "source.ip"]
},
"data_description": {
"time_field": "@timestamp",
"time_format": "epoch_ms"
},
"custom_settings": {
"custom_urls": [
{
"url_name": "User Investigation Dashboard",
"url_value": "kibana#/dashboard/user-investigation?_g=(time:(from:'$earliest$',to:'$latest$'))&_a=(filters:!(('$state':(store:appState),meta:(alias:!n,disabled:!f,index:'logstash-*',key:user.name,negate:!f,params:(query:'$user.name$'),type:phrase),query:(match:(user.name:(query:'$user.name$',type:phrase))))))"
}
]
}
}
Incident Response and Investigation
When a security incident occurs, Elasticsearch provides the tools necessary for rapid investigation and response.
Example: Timeline Investigation Query
GET /logs-*/_search
{
"query": {
"bool": {
"must": [
{
"match": {
"host.name": "compromised-server-01"
}
},
{
"range": {
"@timestamp": {
"gte": "now-24h",
"lte": "now"
}
}
}
],
"should": [
{
"match": {
"event.category": "process"
}
},
{
"match": {
"event.category": "file"
}
},
{
"match": {
"event.category": "network"
}
}
],
"minimum_should_match": 1
}
},
"sort": [
{
"@timestamp": {
"order": "asc"
}
}
],
"size": 1000,
"_source": [
"@timestamp",
"event.category",
"event.action",
"user.name",
"process.name",
"process.args",
"file.path",
"network.direction",
"source.ip",
"destination.ip"
]
}
Threat Intelligence Management
Elasticsearch is increasingly being used to manage and operationalize threat intelligence, providing a platform for storing, correlating, and acting upon indicators of compromise (IOCs).
IOC Storage and Enrichment
Elasticsearch can store and index millions of indicators from various sources, allowing for rapid lookups and enrichment.
Example: Storing IP Reputation Data
PUT /threat_intel_ip/_doc/1.2.3.4
{
"indicator": "1.2.3.4",
"type": "ip",
"confidence": 90,
"severity": "high",
"tags": ["ransomware", "c2"],
"source": "AlienVault OTX",
"tlp": "amber",
"first_seen": "2023-04-15T12:30:45Z",
"last_seen": "2023-05-23T08:15:22Z",
"description": "Command and control server for BlackCat ransomware variant",
"associated_campaigns": ["BlackCat-2023"],
"geolocation": {
"country_code": "RU",
"country_name": "Russia",
"city": "Moscow",
"location": {
"lat": 55.7558,
"lon": 37.6173
}
}
}
Automated Enrichment Pipeline
Creating an ingest pipeline to automatically enrich incoming log data with threat intelligence:
PUT _ingest/pipeline/threat_intel_enrichment
{
"description": "Enriches logs with threat intelligence data",
"processors": [
{
"enrich": {
"description": "Add threat intel data for source IP",
"policy_name": "ip_threat_intel_policy",
"field": "source.ip",
"target_field": "threat.source",
"ignore_missing": true,
"ignore_failure": true
}
},
{
"enrich": {
"description": "Add threat intel data for destination IP",
"policy_name": "ip_threat_intel_policy",
"field": "destination.ip",
"target_field": "threat.destination",
"ignore_missing": true,
"ignore_failure": true
}
},
{
"script": {
"lang": "painless",
"description": "Add threat intel match flag",
"source": """
boolean hasThreatInfo = false;
if (ctx.containsKey('threat')) {
if (ctx.threat.containsKey('source') || ctx.threat.containsKey('destination')) {
hasThreatInfo = true;
}
}
ctx.threat_matched = hasThreatInfo;
"""
}
}
]
}
Real-time IOC Matching
Elasticsearch can perform real-time matching of network traffic against threat intelligence:
GET /network-logs/_search
{
"query": {
"bool": {
"must": [
{
"exists": {
"field": "threat_matched"
}
},
{
"term": {
"threat_matched": true
}
}
]
}
},
"sort": [
{
"@timestamp": {
"order": "desc"
}
}
],
"size": 100
}
Implementation Considerations
When implementing Elasticsearch for cybersecurity use cases, consider the following best practices:
Performance Optimizations
- Use ILM (Index Lifecycle Management) policies to manage data retention and optimize storage
- Implement hot-warm-cold architecture for cost-effective storage of security data
- Use properly sized machine learning nodes for anomaly detection workloads
Example ILM Policy for Security Data:
PUT _ilm/policy/security_data_policy
{
"policy": {
"phases": {
"hot": {
"min_age": "0ms",
"actions": {
"rollover": {
"max_size": "50GB",
"max_age": "1d"
},
"set_priority": {
"priority": 100
}
}
},
"warm": {
"min_age": "7d",
"actions": {
"shrink": {
"number_of_shards": 1
},
"forcemerge": {
"max_num_segments": 1
},
"allocate": {
"require": {
"data": "warm"
}
},
"set_priority": {
"priority": 50
}
}
},
"cold": {
"min_age": "30d",
"actions": {
"allocate": {
"require": {
"data": "cold"
}
},
"set_priority": {
"priority": 0
}
}
},
"delete": {
"min_age": "90d",
"actions": {
"delete": {}
}
}
}
}
}
Security Considerations
- Implement TLS for all communications
- Use role-based access control to limit access to sensitive security data
- Enable audit logging to track access to security indices
- Implement node-to-node encryption for cluster communications
Example Elasticsearch Security Settings:
# elasticsearch.yml security settings
xpack.security.enabled: true
xpack.security.transport.ssl.enabled: true
xpack.security.transport.ssl.verification_mode: certificate
xpack.security.transport.ssl.keystore.path: elastic-certificates.p12
xpack.security.transport.ssl.truststore.path: elastic-certificates.p12
xpack.security.http.ssl.enabled: true
xpack.security.http.ssl.keystore.path: http.p12
# Enable audit logging
xpack.security.audit.enabled: true
xpack.security.audit.logfile.events.include: ["authentication_success", "authentication_failed", "access_denied", "index_access_denied"]
Scaling Considerations
- Plan for data growth - security data can grow exponentially
- Use cross-cluster search for federated security analytics
- Consider using dedicated coordinating nodes for heavy security analytics workloads
Open-Source Tools and Resources
Several open-source projects can help you implement Elasticsearch for cybersecurity:
- VMC (Vulnerability Management Center) - An open-source platform for vulnerability management that integrates with Elasticsearch
- OpenCVE - A CVE monitoring platform that can feed vulnerability data to Elasticsearch
- ElastAlert - A framework for alerting on anomalies, spikes, or other patterns of interest in data stored in Elasticsearch
- HELK - A threat hunting platform that leverages Elasticsearch for analytics
- Security Onion - A security monitoring platform that uses Elasticsearch for data storage and analysis
Conclusion
Elasticsearch has become an essential tool for modern cybersecurity operations, providing the scalability, speed, and flexibility needed to manage security data effectively. From vulnerability management to threat detection and incident response, its capabilities extend across the entire security lifecycle.
By implementing the examples and best practices outlined in this article, security teams can enhance their detection and response capabilities while gaining deeper insights into their security posture.
That’s all folks
I hope you enjoyed this article, feel free to leave a comment or reach out on twitter @bachiirc.